Welcome to the maze of network security, where the threats are as shifty as a chameleon in a bag of Skittles! In the constantly evolving world of technology, one can never be too careful or prepared.
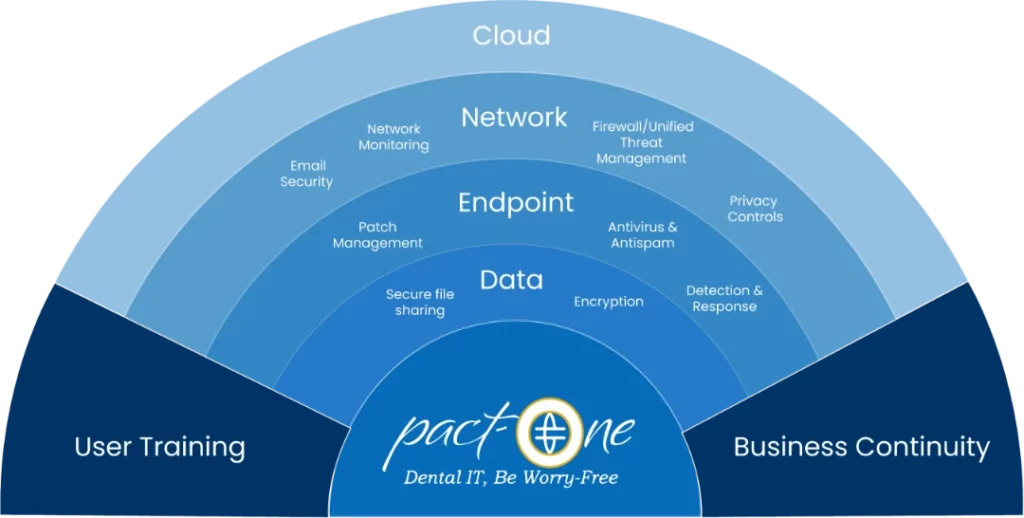
With rising cybersecurity threats, protecting your business network is similar to dressing it up in a suit of armor; only this armor has seven layers. Each layer is just as crucial as the next, working in harmony to provide comprehensive security for your business. So, buckle up and get ready to take a scenic drive through the seven layers of cybersecurity that your business needs. It's not just about IT support or network monitoring anymore; it's about securing your digital fortress!
Layer 1 of Cybersecurity: Physical Security
Physical security, as the name suggests, refers to the tangible defenses put in place to protect your hardware and infrastructure from physical damage or unauthorized access. This might seem old-school, like a burly knight guard with an intimidating axe, but it's the base level of defense in your cybersecurity castle!
Factors to Consider with Physical Security
When considering your physical security, there are several factors to keep in mind.
- Access Control: This is the knight at the gate to your castle. It includes locking mechanisms, biometric systems, and/or security personnel. It's all about keeping unauthorized individuals out and letting the right ones in.
- Site Design and Layout: Just like a well-planned castle has a moat and a drawbridge, your business must have a well-structured layout that takes into account natural surveillance and visibility, lighting, and alarms. It's about making your fortress unappealing and difficult for attackers to access.
Remember, even the mightiest of digital security measures can be undone with a misplaced keycard or an unattended laptop. So, don't underestimate the power of your physical security layer, it's the foundation of your entire castle!
Layer 2 of Cybersecurity: Perimeter Security
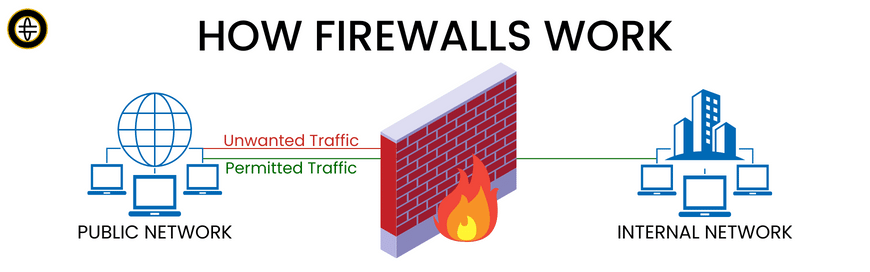
Don't be fooled - the fight against cyber threats isn't just an inside job. Your cybersecurity suite should include perimeter security, that is, security measures installed at the edge of the network to monitor and control all incoming and outgoing traffic to prevent any unauthorized or harmful data from hopping the fence. We're talking firewall fortresses.
Firewalls
Firewalls act as the gatekeepers of your network, much like a castle gate that allows the right people to enter while keeping the marauding invaders out. They accomplish this by establishing a barrier between your trusted internal network and untrusted outside networks, such as the Internet. Firewalls can be hardware, software, or both. They use predefined rules to analyze and filter inbound and outbound traffic, allowing or blocking data packets based on these rules.
Layer 3 of Cybersecurity: Network Security Monitoring
Next up in our tour, we have the layer of network security monitoring. It involves the collection, analysis, and escalation of network traffic, all to detect and respond to threats that manage to slip past the initial defenses. This layer is similar to having a trusty scout who roams the cyber wilderness, tracks down the hidden threats, and alerts the forces to mobilize against them. So, when the stout gatekeepers have done their job, it's the scout's turn to shine, ensuring that no malicious packets have taken root within your digital empire. It's not about just building a fortress, but about keeping it continuously guarded and monitored!
Layer 4 of Cybersecurity: Endpoint Protection
As we dive deeper into the cybersecurity realm, we're faced with endpoint protection. Think of this layer as the personal bodyguard for each device (endpoints) that connect to your network. This includes ensuring your PCs, laptops, and mobile devices are armored up with security tools including:
- Antivirus and antispam software: This software scans, detects, and removes viruses and other malicious software (malware) from your system.
- Detection and response tools: These tools identify suspicious activity and signal an alarm when the system or network is potentially being attacked.
- Patch management tools: These tools ensure your systems are updated with the latest security patches.
Layer 5 of Cybersecurity: Information and Data Security
Information and data are the crown jewels in the kingdom of your business. Our fifth layer, information and data security, ensures these jewels are well-guarded against unauthorized access, tampering, or data breaches. It's about preserving the confidentiality, integrity, and availability of your business data. This layer focuses on protecting the databases and repositories where your business data rests, using encryption, backed up with access controls and data masking techniques.
Layer 6 of Cybersecurity: User Education
Next, let’s talk about user education. This is like a secret weapon - your staff, equipped with the knowledge and awareness of potential cybersecurity threats along with the best practices to prevent them. Remember, no cybersecurity framework is complete without a well-educated user base. All the best technology won't help if people within your business unknowingly open the gate to the enemy! Conducting regular employee cybersecurity training could be your best defense.
Layer 7 of Cybersecurity: Critical Asset Security
Saving the biggest for last, we have critical asset security. This is the hidden vault in your castle, safeguarding your most precious assets and ensuring they remain secure and accessible even when disaster strikes. It is the final line of defense – protector of your business's most critical resources and data.
Backup and Disaster Recovery Services
Backup and disaster recovery (BDR) services come into play here, acting like loyal scribes and master architects, diligently making copies of your business's key data and swiftly restoring your operations after a disaster. Together, they ensure your data is protected and your business can rise from the ashes, minimizing downtime and ensuring continuity.
Multi-Layered Network Security for Your Business
The use of a multi-layered approach to network security is absolutely pivotal in the realm of modern business. Just as a medieval castle counts on multiple defensive structures - moats, drawbridges, towers, and walls - to keep the inhabitants safe from besieging forces, so too should a business employ several layers of security defenses to guard its sensitive data against relentless cyber threats. Each layer of security you implement adds another hurdle for potential hackers, making your business a less appealing and more challenging target. This multi-layered strategy provides redundancy in case a security control fails, or a vulnerability is exploited, helping to prevent a minor breach from becoming a major catastrophe. So, don't rely solely on the drawbridge or the tower; instead, fortify your network by incorporating a comprehensive, layered approach to security.
Conclusion
Navigating the complex maze of network security doesn't have to be a Herculean task. By understanding and implementing a multi-layered defense strategy, you can effectively armor your business against the relentless onslaught of cybersecurity threats. Remember, the key lies not in reliance on a single layer of protection, but in the synergy of multiple layers working together. So, don't be the business owner who learns about cybersecurity the hard way. Strap on your suit of armor and fortify your digital fortress today. The world of IT waits for no one - it's time to get secure!
Are you a business owner in Arizona, California, Nevada, Oregon, or Washington seeking a more secure network for your business? Look no further! Pact-One is here to help you keep your business secure with multilayered network security solutions that are tailored to your needs. Contact us today for a complimentary consultation.



You must be logged in to post a comment.