Cybercriminals have many opportunities to intercept confidential data. But if your data is encrypted, it’s much more difficult for your data to be compromised – should a cybercriminal succeed in getting their hands on it.
As with any other healthcare provider, dental practices must comply with HIPAA and HITECH legislation – requiring that all communications be encrypted. Since email is one of the leading methods of exchanging confidential information - such as patient health records - it’s imperative that you take every step to secure email communications. It simply isn’t enough to rely on conventional perimeter defense measures like firewalls or consumer-grade protections that come with many email services.
What is email encryption and how does it work?
Email encryption is a tactic utilized to secure email communications between the sender (your dental practice) and the recipient. It comes in two forms – transport layer security (TLS) and end-to-end encryption (E2EE).
Many email providers, such as Microsoft and Google, use TLS to help protect users email while it’s in transit. TLS protects the email through its cyber journey from one mailbox to another – preventing what’s known as “man-in-the-middle" compromise. Once the email lands in an inbox, the protection from TLS no longer exists – leaving it vulnerable should your email account be pursued by a hacker.
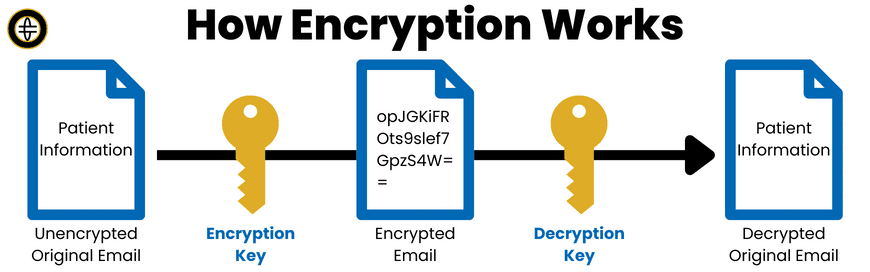
For additional protection, end-to-end encryption is also utilized by many email providers. This form of email encryption works by means of “keys”. A public key encrypts the message on its way out and can only be decrypted by another private key.
What is needed to encrypt email communications?
The National Institute of Standards and Technology has published a 139-page document about email security, with extensive details on what healthcare providers and their associates must do to secure electronic protected health information (ePHI). These steps include digitally signing emails to confirm the identity of the sender, encrypting the body of the messages, and encrypting all communications between mail servers.
To cover all the bases, it’s a promising idea to have all communications encrypted using enterprise-grade cryptography algorithms. Using a third-party email encryption provider helps with this process through automated management.
Are conventional measures enough?
TLS is the industry standard in secure communications, but it’s not enough to protect emails containing ePHI as the law requires. Most significantly, TLS doesn’t encrypt data at the ready, which means archived emails might still be exposed to hackers. There’s no way to guarantee that information will remain encrypted until it reaches its destination.
Another potential problem occurs when people reply to your messages, sending copies of the email originally received, which isn’t encrypted to the same standards. In other words, if you’re relying on TLS, you need to be incredibly careful about who you communicate with.
Many businesses also use a virtual private network (VPN) to secure all communications over the internet. Again, a VPN adds a much-needed extra layer of protection, but it doesn’t provide a message-signing mechanism. However, since using a business-grade VPN encrypts everything, it does encrypt email header information, such as senders, subject lines, and recipients. Using a VPN isn’t a complete solution but should be part of your overall cybersecurity plan. This is especially true if you have employees who are connecting to the internet through unsecured wireless networks – such as remote employees.
How does encryption work in dental practices?
To comply with HIPAA legislation, dental practices usually use public-key cryptography, which involves having a pair of keys associated with each email address. One key is used to encrypt the email, while the other is used to decrypt it once it reaches the recipient. The public key is kept on a key server that anyone can access, while the second key is kept private. This means that only the sender and intended recipient, being the only parties who have access to the private key, can access the email.
If the email gets sent to the wrong party by mistake, or somehow intercepted in transit, the information will be scrambled and, at least in practical terms, impossible to crack. To exhaust an entire 256-bit key space in the standard AES-256 encryption algorithm, it would take some 50 supercomputers 3×1051 years, by which time any would-be hacker would have run out of patience!
Pact-One provides dental practices with a multilayered approach to security which includes all the measures you need to protect your patients’ data and ensure HIPAA compliance. Contact us today to schedule your FREE network security audit.



You must be logged in to post a comment.